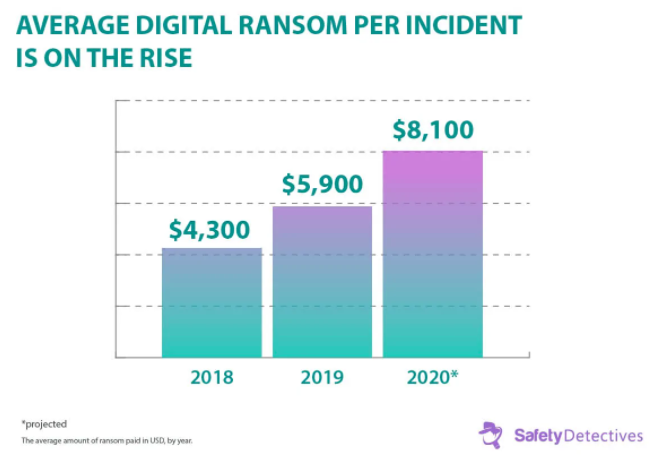
Screen frozen, police-like notice appearing, intimating you to pay a fairly large sum of money (up to millions of dollars), usually in a cryptocurrency, in exchange for a password capable of unlocking all the contents of your computer… This is what ransomware looks like. The word ransomware refers to a class of malware that renders the data of infected computers inaccessible and demands payment (a ransom) to restore them. Technically, they are cryptographic Trojan horses and have the sole purpose of extorting money, through a “file seizure” by means of encryption that, in practice, makes them unusable. Ransom is highly profitable. The average ransom payment has nearly doubled over the years, and this trend shows no signs of slowing down.
1.Regular preventive work.
Pursuant to the CSL, network operators shall adopt security measures for cybersecurity and data protection. Security measures include technical measures such as anti-virus software, use of beacons, honeypots, and organizational measures such as internal document management system, regular employee training, etc.
2.Emergency measures for security incidents.
Network operators must develop an emergency plan for cybersecurity incidents to promptly respond to security risks, resolve system loopholes, viruses, cyberattacks, and other cybersecurity risks, and take remedial measures.
3.After-action review and keep a record of cyber threats or attacks.
The CSL requires network operators to adopt technical measures to monitor and record network operation status and cybersecurity incidents, and the cyber-related logs should be kept for at least 6 months. After the occurrence of the incident, companies need to keep in communication with and assist the authorities in finishing their investigation and review, for example, to provide the authorities a summary of the cause, nature, and influence of the security incident and improvement actions.
4.Report cybersecurity breaches to regulatory authorities.
Normally, the reporting obligation is triggered by the occurrence of an incident threatening network security. In accordance with the CSL, the DSL, and the PIPL, network operators shall promptly notify the local government, industry regulators, public security authorities, and the local cyberspace administrations.
5.Notify affected individuals.
Under the CSL, in case of disclosure, damage, or loss of user’s information, the network operator is obligated to take immediate remedies and notify the affected users promptly. Additionally, under the PIPL, personal information processors need to notify affected individuals in case of personal information incidents.
China also takes a sectoral approach to the protection of information security. For example, industries or sectors such as telecoms, credit reporting, banking and finance, automobile, and insurance are subject to some specific requirements concerning data protection, information leakage prevention, and emergency response to cybersecurity incidents.
We at Wang Jing & GH Law Firm have a long and solid experience in advising our local and foreign clients about data protection and security law in China, the EU (GDPR), and the USA, placing us as leaders in the field. In case of any questions don’t hesitate to contact us.




